Beyond authentication: Why device and behavioral intelligence are now non-negotiable for banks

On paper, banks have taken the necessary steps to combat payment fraud in digital banking: multi-factor authentication (MFA), transaction monitoring rules that flag large or unusual payments, device fingerprinting, and basic risk checks running in the background. Yet, fraud detection and prevention spending by financial institutions is forecasted to surge by 85% by 2030, rising from $21 billion in 2025 to $39 billion in 2030.
This is unsurprising given the latest figures:
- Authorized push payment (APP) fraud is projected to result in global losses of US$331 billion by 2027. In the UK, 77% of APP fraud cases started online and 17% started through telecommunications networks.
- Investment scams are the single largest category of consumer fraud by losses causing US$5.7 billion in reported losses in 2024 alone, up 25% year-over-year.
- Losses from impersonation and “safe account” scams targeting older US adults have skyrocketed from $55 million in 2020 to $445 million in 2024.
The uncomfortable truth is that these attacks often go unnoticed by traditional fraud detection controls simply because they do not resemble fraud from transaction perspective.
The core problem is not a mystery; it’s structural. Most controls are still designed to stop impostors, while modern fraud is increasingly about manipulating real customers and compromising real devices.
This has created a new reality where the line between genuine and fraudulent transactions has blurred.
Banks now need to adopt a broader lens to gain visibility into the entire user journey. Banks need to understand how the user behaves, what is happening on the device, and whether the transaction aligns with legitimate intent – not just who the user is and what they are trying to do.
Key takeaways:
- Modern fraud manipulates customers’ behavior and systems: Strong customer authentication (SCA) and transaction monitoring are required. However, they are not enough to stop APP fraud resulting in legitimate customers being coerced or tricked into authorizing transfers.
- Device and malware risk intelligence are crucial: With device compromise being one of the preferred ways to commit fraud in recent years, banks must adopt adequate security controls to mitigate them.
- Behavioral analytics are no longer optional: Banks must monitor users’ behavioral patterns throughout transaction sessions to identify deviations that might indicate fraud attempts. This helps to prevent fraud and also satisfy regulatory requirements that increasingly mandate a behavioral approach to fraud detection.
When legitimate users become vectors: Understanding modern fraud patterns
APP fraud is more than just a monolithic attack.
While it is often treated as a single threat, the reality is more nuanced. APP fraud is an umbrella term for any fraudulent authorized push payment, meaning any payment where the customer authenticates and authorizes the transaction themselves but does so under deception, false pretense, or coercion.
There are many different modus operandi, but what ties them all together is this: Fraudsters no longer need to be the customer; they only need to influence the customer or compromise their device.
To better understand these fraud patterns, this blog explores two examples of impersonation scams, using different attack techniques. We also explore the importance of behavioral analytics, alongside device and malware analytics, to help mitigate impersonation scams. And finally, we cover regulators’ views on these security controls.
Impersonation scams

In impersonation scams, fraudsters use social engineering and psychological pressure to manipulate victims into authorizing payments to these criminals. The typical impersonation scam unfolds like this:
- 1. The customer receives an inbound call from a fraudster who claims to be from the bank’s fraud team or other trusted party. The fraudster states there is a security issue with the customer’s account or device in an attempt to build trust, while creating a false sense of fear and urgency.
- 2. The fraudster instructs the customer to log in and navigate to specific screens, often providing exact button names and menu paths.
- 3. The fraudster guides their victim through the process of creating a transfer to what they describe as a “safe account” for temporary funds verification or protection from fraud.
- 4. Critically, the caller may coach the victim on what information they will see and prepare them for what bank prompts or warnings might appear – preventing them from recognizing red flags.
- 5. The victim, following instructions, completes the fund transfer, believing they have protected their funds.
Voice phishing with remote access tools (RATs)
In this more sophisticated method, fraudsters combine social engineering with the use of remote access tools (RATs) to execute their attack.
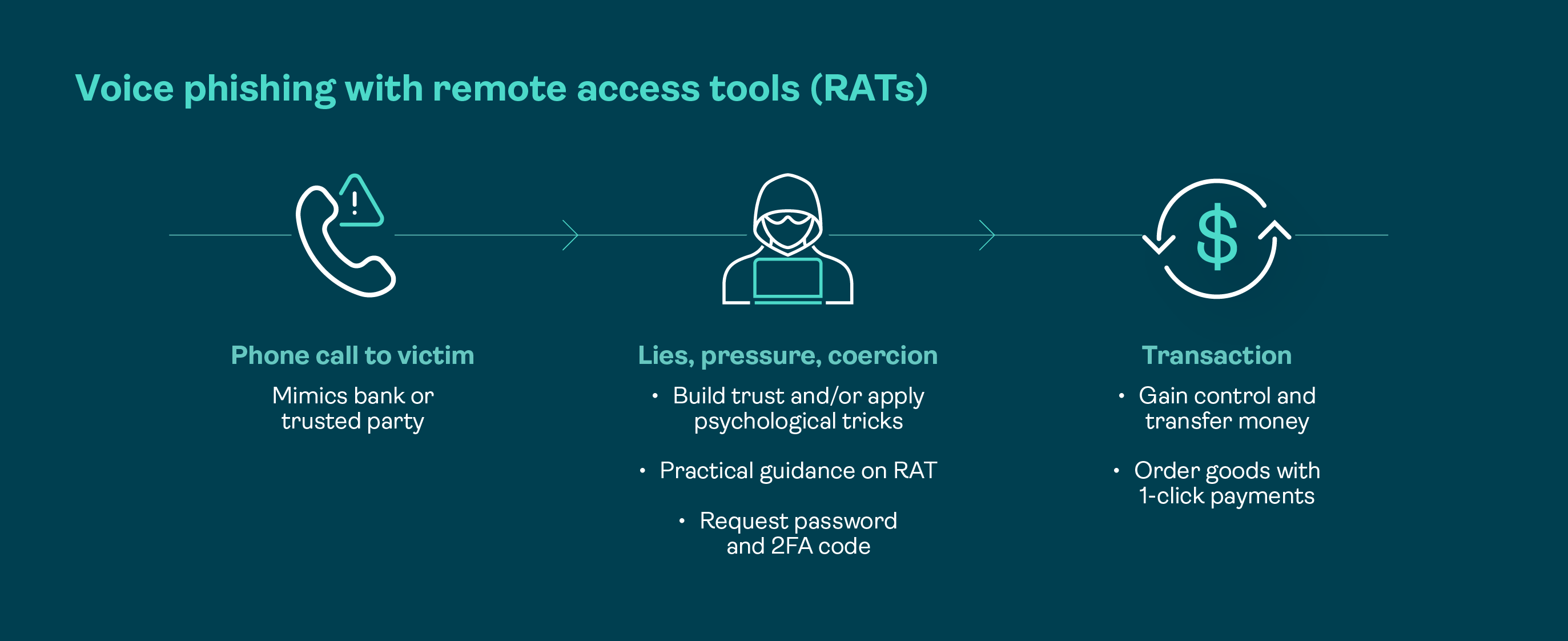
It typically unfolds like this:
- 1. The customer receives an inbound call from the fraudster claiming to be from their bank’s fraud team or other trusted party. The fraudster states there is a security issue with their account or device, to build trust while creating a false sense of fear and urgency.
2. The fraudster instructs the customer to download a remote access application which is often a legitimate tool such as “AnyDesk”, “TeamViewer”, or “Quick Assist”. Alternatively, the fraudster may instruct the customer to download a malicious app known as a dropper app.
A “dropper” app is a malicious app disguised as a legitimate one. This could also be used by fraudsters, allowing them to remotely deploy malware with remote access capabilities.- 3. The customer, trusting the caller, downloads and installs the tool and provides the fraudster with remote access capabilities.
- 4. The fraudster now has control of the customer’s device, allowing them to:
a. See what the customer is seeing in real time
b. Control the tap and swipe on the customer’s screen or their mouse/cursor movement
c. Enter credentials or transaction details
d. Manipulate the on-screen display - 5. The fraudster may then further instruct the customer to log in to their banking application to perform transactions directly on the victim’s device, while the customer watches what appears to be legitimate banking activity.
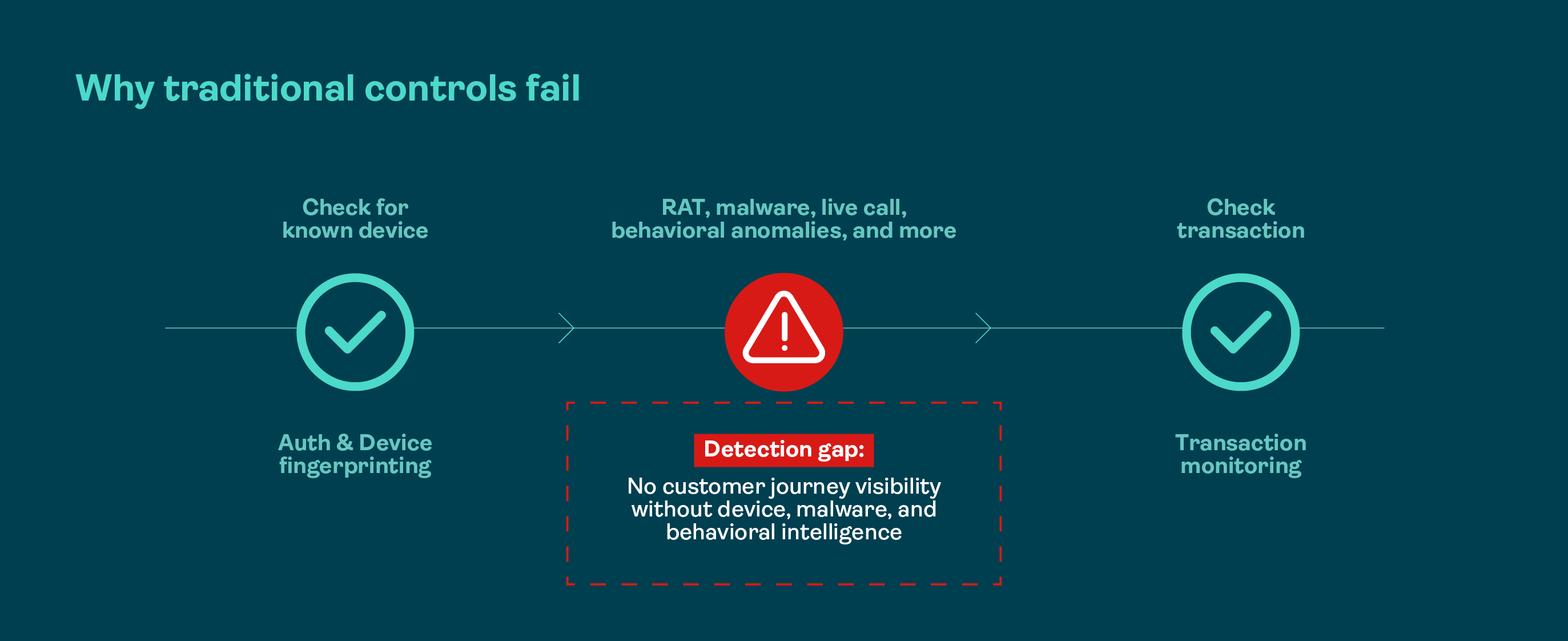
Why traditional controls fail
Traditional fraud detection controls excel at determining the “who” and the “what” but fail to consider the “how”. In both cases above, a traditional rule-based system would see that the transaction was done:
- By a known customer
- On their usual device
- Logging into the genuine banking app or website
- Using correct credentials
- Passing all authentication challenges
- Approving the transaction themselves
However, the traditional rule-based system would fail to take into account:
- How the user is behaving compared to their normal patterns
- How the session is unfolding: confidently, decisively, or as if the user is being coached step-by-step
- How the device is behaving: as a personal device under the user’s control or with signs of remote manipulation, overlays, and malware
- How the user arrived at the decision to make this payment – if there was external contact (e.g., phone call, instant messaging) that occurred during or minutes before the transaction
While context-level indicators, such as a new recipient and an unusual amount, could be used as risk factors, too many such transfers are legitimate and could lead to many false positives. In fact, this may lead fraudsters to play the long game to “build trust” into the system by starting with a smaller amount of money to prime their receiving account for larger amounts in the future.
Without the bank understanding how the customer arrived at this decision, a manipulated user or a user with a compromised device looks indistinguishable from a genuine one. The entire transaction journey, the sequence, timing, interaction patterns, and correlation with an external event (i.e., a call) may tell a very different story.
Behavioral analytics adds more banking transaction security
Behavioral analytics can mean many things in the industry. In the context of fraud prevention, it is about learning how a user normally behaves and detecting meaningful deviations in real time within the banking session.
Rather than relying on static rules like “flag payments over $10,000” or “flag transfers to high-risk countries,” banks can monitor for behavior that is inconsistent with how the user typically behaves. Banks can then add them as additional fraud risk signals before warning the user or blocking the transactions.
For instance, Fraud Risk Suite (FRS) enables banks to observe real-time interactions such as:
- Time spent on each step of a transaction journey
- How users navigate through the banking application
- Typing and interaction cadence
- Touch or mouse patterns
- Device motion and rotation
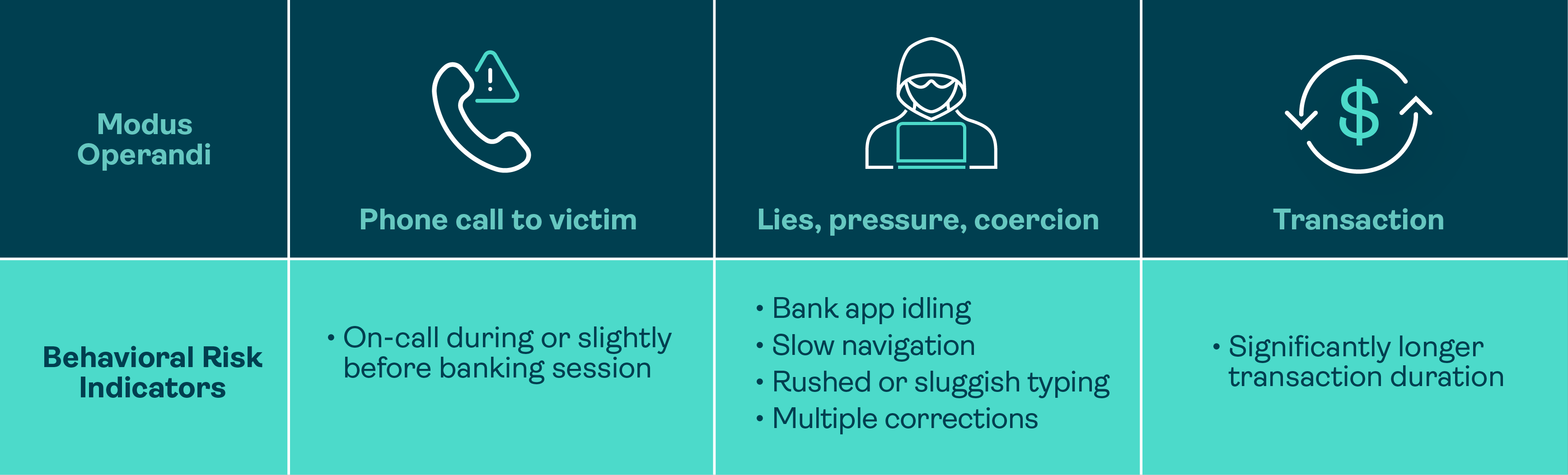
These data points are used to match the current user behavior to expected behavior based on historical sessions (i.e., behavioral identity model) to establish APP fraud indicators such as:
- Coaching or guidance: A user being coached step-by-step typically shows patterns of slow inputs and pauses when listening to instructions, and sudden bursts of activity when following a new instruction.
- Stress or duress: A user under pressure may show increased typing errors, hesitation, rapid backtracking, and eventual hurried submission.
- Remote control via RAT: A user whose device is being remotely controlled may show:
- Interaction patterns that deviate significantly from their baseline
- Touch or mouse movements that are uncharacteristic of a human
- Precise, rapid navigation that looks programmatic
When digital banking sessions are known to have been conducted by fraudsters, data from these fraudulent sessions will also be used to establish a “fraudster model” that can be used to compare genuine user behavior to known fraudster behavior. Critically, these models will continually be updated with use, allowing banks to proactively and accurately detect and prevent APP fraud attempts.
Device risk intelligence: Part of the behavioral analytics conversation
On top of serving as the foundation to FRS's behavioral analytics capabilities, device risk intelligence complements behavioral analytics by monitoring device state and malware risks, or risk factors beyond the human element. Visibility into these risk signals is crucial to closing the gap that banks often have in their traditional controls.
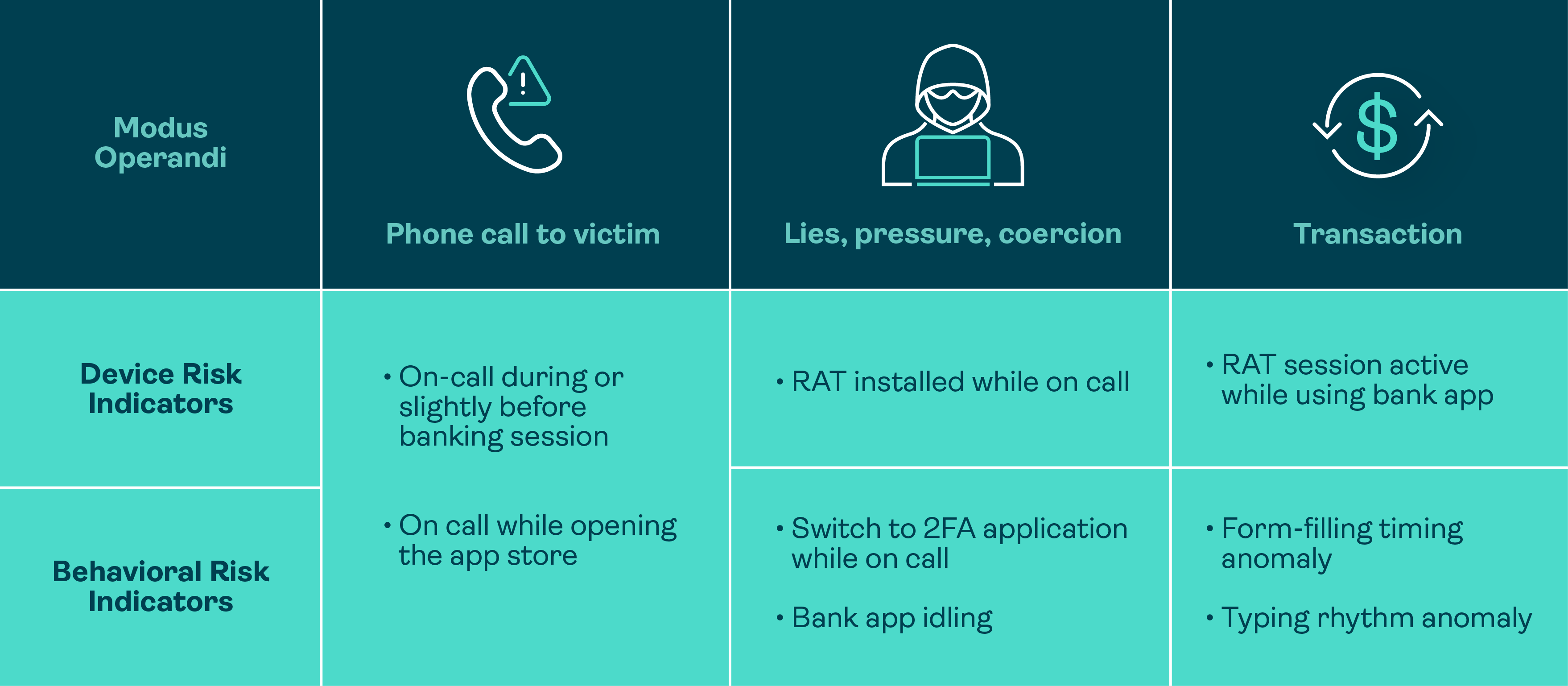
Moreover, many of the most damaging attacks also involve compromise of the device itself, particularly on mobile platforms. For instance, there has been a surge in mobile malware specifically targeting banking applications, with particular emphasis on:
- Overlay attacks: Fake screens on top of the banking app to steal credentials or change transaction details that the user cannot see
- Remote-access capable trojans: Malware that lets remote attackers view the screen in real time, control taps and input, and inject commands
- Accessibility services abuse: Originally designed for assistive technologies, now repurposed by fraudsters to read and manipulate on-screen content using malware
When the device risk engine is utilized alongside behavioral signals, banks get even richer context for each customer’s transaction journey. Combined with behavioral risk data, banks can confidently identify when potential fraud is taking place by answering questions such as:
- Is there known malware present in the device targeting the app?
- Are there side-loaded applications installed in the app?
- Is there an active remote session or screen-sharing tool running?
- Is the device showing signs of screen overlays or accessibility permission abuse?
- Is there any live call during or shortly before the transaction?
- Is the device connection secure? Is a VPN, proxy, or TOR being used?
- Is the device’s actual location inconsistent with the geolocation being claimed?
With market expectations increasingly shifting toward instant and real-time payments, it is important for banks to do all this promptly. FRS enriches risk decisions by embedding these capabilities directly into the session and transaction flows, allowing the fraud intelligence team to make decisions based on the richest possible signals at that moment, in real time.
Marking change through regulations and market conditions
For years, behavioral analytics were positioned as an innovation or a “nice to have” capability that separated forward-thinking banks from laggards. That era is coming to an end, as behavioral analytics become regulatory expectation, not optional enhancements.
Based on the current draft Payment Services Regulation (PSR / PSD3) in Europe, we expect banks to be required to include device intelligence as well as behavioral intelligence into their transaction monitoring systems.










