Passwordless Banking: A Deeper Look at the Benefits of Biometric Authentication and Liveness Detection

I despise passwords. I want to access more online or mobile services without having to fumble with multi-letter, character and number combinations. Passwords are inconvenient and riskier than other authentication options available today because they can be guessed, stolen, or cracked. For that reason, I have been keeping an eye on advances in biometric authentication as a stronger, more secure authentication factor for multifactor authentication strategies. Biometric security involves using personal data and identifiers from the user themselves, such as a retina scan or iris scan, voice recognition, fingerprint scanners, hand geometry, or facial recognition systems, as part of the authentication process to ensure access control.
The Gartner report, “Technology Insight for Biometric Authentication,” asserts that biometric authentication is typically adopted to “…achieve passwordless authentication, thereby enhancing UX/CX [user experience/customer experience] and potentially elevating trust and accountability.” Sounds like a winner to me and a big gain for financial services organizations competing for customers.
The Gartner report calls mobile banking the “killer app” (i.e., soon to be indispensable in mobile banking use cases) for biometric authentication. Though biometrics also has use cases for healthcare and government agencies, we believe that now is especially the time for financial institutions to adopt biometric authentication for mobile banking use cases to increase trust and accountability and improve the customer experience – key components to increasing revenue for financial institutions.
Are Consumers Ready for Biometric Technology for Commerce and Banking?
A recent Visa survey of 1,000 U.S. consumers, for example, says yes. The majority of respondents preferred biometric authentication to password-based authentication:
- Respondents said the use of biometrics is easier (70%) and faster (61%) than passwords
- 52% claimed they would change banks if their bank did not offer biometric authentication in the future
- The most commonly cited benefits of biometric authentication among respondents were
- Not having to remember multiple passwords/PINs (50%)
- Better security than passwords/PINs (46%)
- Not forgetting/losing a method of authentication (33%)
In measuring the quality of the customer experience, transaction abandonment rates are an important metric. Almost 50% of respondents to the Visa survey reported abandoning an online purchase, because they couldn’t remember their password.
“The CX benefits of biometric authentication have driven an uptick in mobile banking applications over the past few years,” the Gartner report states. As they evaluate biometric authentication security solutions, financial institutions need to keep in mind the differences between device-native and third-party biometric authentication methods. A benefit of third-party biometric methods, consisting of incorporating an SDK into a mobile app (such as that offered by OneSpan), is that banks can serve more of their customer base. Not all mobile users own devices that include device-native hardware and software for biometrics. However, nearly every mobile device includes a camera, which can be used to capture a user’s face for biometric authentication.
Is Biometric Authentication More Trustworthy than Other Authentication Methods?
I argue yes, one of the advantages of biometric authentication is it is indeed more secure than other authentication methods. The key to a reliable biometric authentication system is the ability to detect or prevent the impersonation of a living person’s biometric trait. The types of biometric you choose, whether fingerprint, “faceprint”, or other modality is not simply another form of password or token.
Without additional analysis, there’s really no way to tell who is providing a password. You only know that the password was entered and that it matches the password in the back-end. On the other hand, a reliable biometric authentication system with effective liveness detection and anti-spoof mitigations provides an additional indicator of trust in that it validates the subject/person that is offering the sample for biometric verification. Because the fingerprint, face, or other biometric information is presented live and connected to the in-the-flesh user.
Dispelling a Biometric Authentication Misconception
According to Gartner, “Biometric authentication cannot and does not depend on the secrecy of biometric traits, but instead relies on the difficulty of impersonating the living person presenting the trait to a capture device (‘sensor’). This latter point is not widely known, leading to some common misconceptions, reinforced by limited presentation attack detection (PAD) in consumer devices and publicity about successful attacks against Apple Touch ID, Samsung swipe sensors, Android face recognition and so on.”
You’ve probably heard that among the disadvantages of biometrics is that “you can’t change your fingerprint or face if it’s ever compromised.” True – you can’t change your biometric traits like you can a password. However, the notion that should a cybercriminal or hacker steal your biometric data they will successfully pass the corresponding authentication challenge at the point of biometric capture is a mistaken one.
1. You can’t literally steal someone’s live face/fingerprint/etc.1 – Horror movies aside, in reality cybercriminals don’t usually seek to remove (i.e., “steal”) someone’s face or fingerprint from their body. Well-designed biometric identification systems don’t literally “store” a user’s face or fingerprint. Instead, face and fingerprint biometrics store a mathematical representation of the biometric sample enrolled in the system (referred to as a template). The mathematical representation alone is worthless at the point of capture (see the highlighted point number one in the image below).
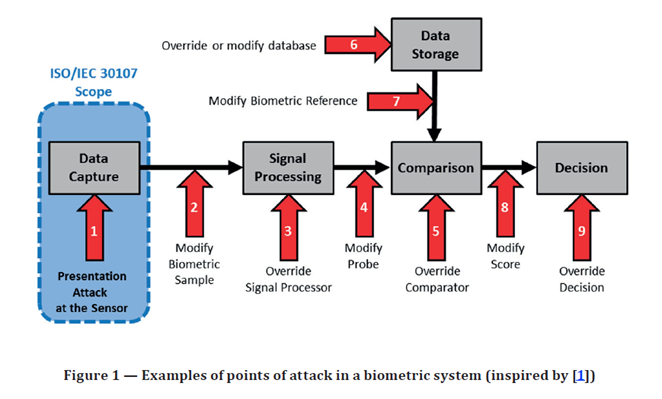
From ISO/IEC 30107-1:2016(E)
2. The live presentation of the biometric trait is the linchpin – As the Gartner report contends, “In a robust fingerprint method, it shouldn’t matter that an attacker can present a facsimile of a person’s fingerprint; anything other than the person’s actual finger (still attached to their living body) should not work.” A presentation attack consists of an adversary presenting a reproduction of a biometric trait (a “spoof”) that resembles a stored reference for a legitimate user (e.g., 3D-printed models, masks, images, video, etc.). Liveness detection identifies whether the presented biometric trait is from a live human or is a digital or manufactured representation (or again, a spoof). Presentation attack detection (PAD) is a combination of anti-spoof and liveness detection mechanisms. In some cases, PAD in consumer-grade, device-native biometrics systems can be lacking compared to third-party biometric authentication technology. The ISO/IEC 30107 standard details a methodology against which a biometric solution’s PAD efficacy can be measured.
Of course, the end-to-end security of a biometric authentication system does not stop at presentation attacks on the sensor where biometric data is captured. Replay attacks are an example of another risk, but in many cases, technology that ensures the integrity of the application – such as in-app protection and app shielding/RASP – help mitigate these risks. But, financial institutions do need to take care in the design, implementation, deployment, and configuration of the biometric authentication solution to ensure secure access.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Sources:
Gartner, Technology Insight for Biometric Authentication, Ant Allan,16 October 2019
1. Granted, there are cases of coercion such as forcing a person to unlock a phone at gun-point, but the same vector exists for passwords or PINs. Or, there are examples of someone unlocking their sleeping spouse’s phone with a fingerprint – facial recognition technology that includes effective liveness detection and anti-spoofing technology mitigates this risk.









