eSignature security tip: How to protect your signing URLs against cyberattacks
Today, data breaches are all too common and businesses can no longer afford to overlook the security gaps in their digital processes. While IT and InfoSec teams are laser-focused on perimeter defenses and threat detection, one critical vulnerability often flies under the radar: eSignature authentication.
For legal and compliance leaders, the implications are serious. Without signer authentication, organizations may lose the ability to prove the signer’s identity. This jeopardizes the enforceability of legally binding agreements.
But that’s not the only issue. The lack of signer authentication also leaves your organization open to a data breach.
Cybercriminals are increasingly targeting eSignature workflows to access digital agreements and contracts like mortgage, insurance, and account opening applications. These – and many other documents that require signatures – are rich with personally identifiable information (PII) and other data that can later be used for social engineering and impersonation scams.
And now, with AI-powered bots capable of scanning for exposed signing URLs at scale, the threat landscape has evolved. If your eSignature process doesn’t include authentication, you are leaving the door wide open for attacks.
In this article, we explain how to bolster cybersecurity protections and safeguard data by adding authentication to eSignature workflows.
What are signing URLs and how do they work?
When organizations require a customer or business partner to sign documents, the eSignature service prepares a transaction and sends out a notification.
There are different methods for organizations to notify signers that a document awaits their signature. Whether they use a public signing URL for these notifications is dependent upon these scenarios:
- 1. Business-to-employee (B2E) using internal authentication: In this use case, protection applies only if an authentication method is used. Specifically, users must sign onto the company’s VPN and either use IP whitelisting or signer Single Sign On. This means the signing URL can only be accessed through the organization’s VPN and network security technologies, or by leveraging the organization’s own security controls in their identity provider systems.
- 2. Business-to-customer (B2C) or partner: There are two distinctions with B2C signing scenarios.
- a. Embedded or integrated transaction: In this scenario, the signing experience is embedded into a web app or mobile app. The user is authenticated to the mobile application first and the eSign transaction can only be accessed through that same application. There is no signing URL to protect because when you send a notification to signers, you are sending a link that redirects the customer or partner back to the mobile app where they must authenticate first. If this is your use case, the signing URL is not exposed publicly and is therefore not subject to the tips in this blog.
- b. Public link: The majority of notifications sent from the signing service use email or SMS. It’s important to recognize that the email or SMS notifications never contain documents as attachments. Instead, they contain a link to the signing ceremony where the documents are hosted. That link is the signing URL and, by default, is not protected by any required authentication method. Instead, you must use an authentication method to protect it.
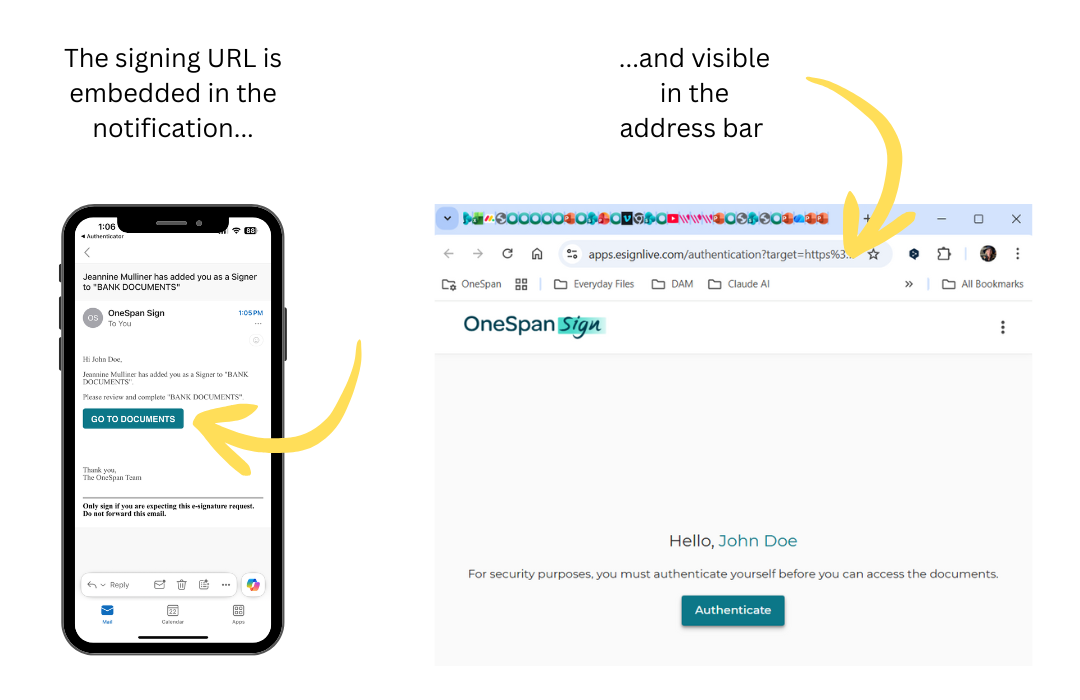
Signing URLs are just like any other standard web link – anyone with access to the URL can view its contents. When signing URLs are shared via email or SMS between a business and its customers or partners, they can be picked up by the systems and tools that typically access emails and SMS messages. This includes email/SMS gateways, SMS firewalls, carrier monitoring solutions, and others that access message content – making the URLs potentially accessible beyond the intended recipients.
As the organization using eSignatures, you are responsible for securing the signing URL so only the intended recipients can access it. To consider the signing URL secure, it must include signer authentication. A best practice is to select the strongest authentication method that fits your specific use cases, aligns with your risk and compliance requirements, and provides a smooth user experience.
Signer authentication best practices
It's important to strike the right balance between customer experience and security when selecting user authentication methods for eSignature transactions. The ideal approach depends on your specific use case and risk tolerance.
To optimize both security and completion rates, match the authentication to the level of risk associated with the signature transaction. This helps reduce abandonment while maintaining compliance.
OneSpan Sign: A wide range of authentication options
OneSpan Sign offers a variety of authentication methods to verify a person’s identity and create a trusted transaction. Multiple authentication approaches can be implemented individually or layered together to confirm signer identity and establish transaction integrity. These include:
- Security questions (Q&A): The signer must correctly answer one or more challenge questions. This requires both parties to establish questions and answers in advance.
- Dynamic knowledge-based authentication (KBA): Integration with identity verification providers, such as Lexis Nexis, enables dynamic questioning based on personal information. These spontaneously generated questions, drawn from consumer databases, make it very difficult for an imposter to answer since the questions rely on information that only the legitimate individual should know (e.g., What street did you live on in the year 2000?).
- SMS OTP: OneSpan Sign sends an OTP to the signer via text message. After entering this code on the authentication screen, the signer gains access to the document(s).
- Certificate-based authentication: When certificate authorities and trust service providers (TSP) issue a digital certificate to an individual, it can be used for authentication. In this case, signers authenticate with their digital certificate and accompanying PIN or password before signing, which results in a qualified electronic signature.
- Government credential systems: Many government employees and contractors authenticate using smart card technology or mobile-derived credentials. Solutions like Common Access Cards (CAC) and Personal Identity Verification (PIV) cards contain embedded digital certificates, creating multi-layered authentication through knowledge factors (PIN), possession factors (physical card), and sometimes biometric identifiers.
- Digital identity verification of government-issued IDs: Digital identity verification technology scans, extracts, and validates ID information from government-issued IDs. It can also include biometrics, where signers take a selfie and the identity verification technology compares their selfie against the official ID photo on their passport, driver’s license, or national government ID.
- Hardware security tokens: OneSpan Sign integrates with Digipass® security keys to enable strong authentication using time- or event-based passcodes.
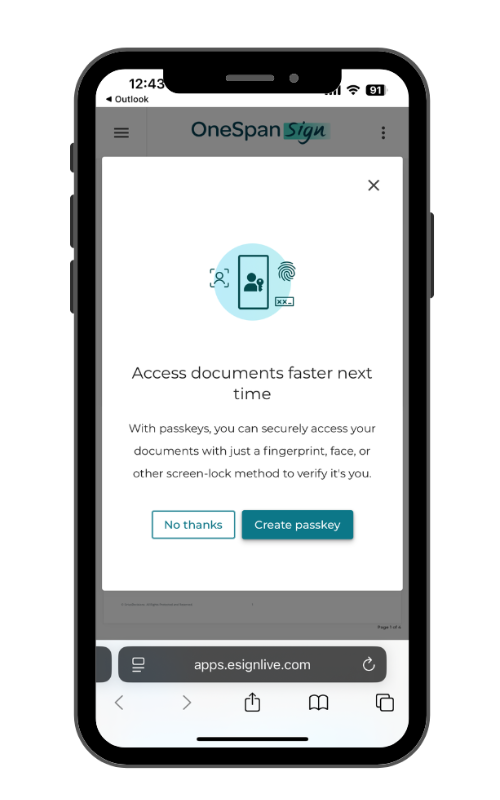
FIDO passkeys: Passkeys provide strong multi-factor, phishing-resistant authentication using mobile device-based biometrics and can function without internet connectivity after initial configuration. With broad compatibility across platforms, browsers, and devices, plus synchronization capabilities, passkeys work exceptionally well for frequent signers.
How to protect eSignature signing URLs
Overlooking signer authentication in eSignature workflows is a risk that organizations can no longer afford in today’s threat landscape. The possibility that a cybercriminal will exploit exposed signing URLs and harvest sensitive data from digital agreements is rising, making the absence of authentication a vulnerability.
Whether you are configuring an automated eSignature workflow via API or manually sending a one-off request for signature, adding authentication is a simple yet powerful step to securing your digital agreements, data, and reputation.
Contact us to learn more or to purchase authentication for your OneSpan Sign transactions.









