The ultimate eSignature security checklist

No organization wants security scars. That’s why IT and Information Security departments generally conduct extensive due diligence on their cloud software providers. Doing so helps protect against data breaches, identity fraud, phishing, malware, viruses, and other security threats.
To help defend your organization, customers, and workflows, we’ve compiled an eSignature security checklist specifically for evaluating electronic signature services.
This blog goes in-depth on each item to provide a deeper understanding of the security measures to consider. We recommend looking at not only the service's security but also:
- How signers are authenticated
- The vendor's methods for protecting digital documents and signatures
- The use of white labeling to help prevent phishing
- The eSignature audit trail connected to the digital transaction
Identity verification & authentication
eSignature laws outline the types of secure eSignatures that can be used to sign digital documents. In the United States, it is the ESIGN Act (Electronic Signatures in Global and National Commerce Act) and UETA. In the European Union, that is the eIDAS regulation.
The legal definition of an eSignature always includes language around signer identity. This puts identity security at the top of your eSignature security priorities. The legal requirement is to connect each signature to the individual who applied it.
Throughout the entire digital agreement process, you will engage with either unknown or known signers. Robust measures are required to verify unknown signers the first time you conduct a transaction with them. With known signers such as employees and existing customers, you already set them up with credentials. The electronic signature software will verify those credentials prior to giving access to the signing ceremony and electronic documents.
Identity verification
The alternative to in-person identity validation is to run identity checks remotely in real time. This reduces the number of steps compared to paper-based processes. It also removes touchpoints where customers struggle and drop off.
The best approach to digital identity verification combines ID document verification technology and facial recognition. These technologies deliver a fast, online customer experience while also establishing trust. They make it possible to digitally verify the signer’s identity using a government-issued ID, such as:
- Driver’s license
- Passport
- National ID
User authentication
To enable better customer experiences, an eSignature solution should easily integrate with a wide range of authentication options throughout the eSign workflow. There are many secure and user-friendly options for authenticating signers online. The key point is to do so without diminishing their experience. As such, look for eSignature solutions that offer options to best fit your signers’ needs across your digital channels.
What to look for:
1. A solution that supports a complete range of ID proofing & authentication options to protect your clients and assets. This includes methods such as:
- Remote identity verification with functionality like facial biometric data and AI algorithms to detect fraudulent ID documents
- Remote user authentication with a one-time passcode (OTP) delivered by SMS
- Remote authentication using Q&A (i.e., challenge-response questions)
- Remote authentication with software/hardware authenticators
- Email address verification through eSign session invitation
- Dynamic KBA through third-party databases (e.g., LexisNexis)
- Support for passkeys for signers (passkeys offer near-instant authentication directly on the signer’s device by leveraging device biometrics)
- Support for smart cards, such as the PIV and CAC smart cards used by the US government
- Support for digital certificates such as those issued by a certificate authority or trust service provider (note that support for all types of electronic signatures, especially qualified electronic signatures, is especially important for organizations doing business in Europe).
2. The ability to configure different authentication methods for different signers within the same transaction.
3. Flexibility to adapt the authentication methods to the risk profile of your business processes. For example, the ability to customize challenge-response questions and the number of questions.
Document and signature security
Look for an eSignature solution that packages and secures the final eSigned document using digital signature technology. Digital signing capabilities should be built using public key infrastructure (PKI).
Electronic signing solutions should apply the digital signature at two levels:
- At the signature level, to prevent tampering with the signature itself
- At the document level, to prevent tampering with the document’s contents
Creating a digital signature ties together signing intent with the information agreed to at the time of signing. It also locks down and tamper-proofs the eSigned document, so unauthorized changes can’t slip by unnoticed. This is a vast improvement over wet signatures or handwritten signatures on paper documents.
Some vendors apply a digital signature as an envelope to a document (once all signatures have been captured). This is not a recommended practice for document signing. It leaves the document and signatures unprotected while the process is being completed. This results in the wrong date and time stamp on individual signatures.
If a signer and a co-signer eSign on two separate days, you want that history reflected in the audit trail. The best practice is to apply a digital signature as each eSignature is added to the document. This builds a comprehensive audit log with the date and time that each signature was applied.
What to look for:
- Each signature must be secured with a digital signature
- A comprehensive audit trail should include the date and time of each signature
- The audit trail must be securely embedded in the document
- The audit trail must be linked to each signature
- Ability to verify the authenticity of the signed record offline, without going to the vendor's website
- One-click signature and document verification
- Ability to download a verifiable copy of the signed record with the audit trail
- The document must be accessible to all parties
Audit trail
When regulated companies undergo a compliance audit, they are often asked to prove the exact business process they followed. As part of this, auditors also look for a record of every time key documents were touched, when, and by whom.
Capturing a comprehensive audit trail allows you to demonstrate exactly how a customer completed a transaction.
What to look for:
Look for a single, unified audit trail that captures the identity verification, authentication, and eSignature events in the transaction. This should include:
- Method used and device used to identify or authenticate each participant
- IP address of each participant
- Date and time stamp of all events
- All web pages, documents, disclosures, and other information presented
- Time reviewing each document
- What each party acknowledged, agreed to, and signed
- All other actions taken during the transaction, such as failed authentication attempts (if any) and data fields that have been edited
In addition, look for eSignature software that embeds the audit trail in the signed document for easy verification and storage. Documents that can be verified and archived independently of the eSignature vendor provide an additional layer of security. Whether or not you maintain an account with the eSignature service in the future, your documents will not be affected. An embedded audit trail means you do not have to go online to access or verify the signed document.
The best way to achieve vendor independence is to have a solution that embeds eSignatures, time stamping, and audit trail directly in the document. This creates a self-contained, portable record.
In addition to making audits much easier, these audit trail records provide additional protection in the event of a dispute.
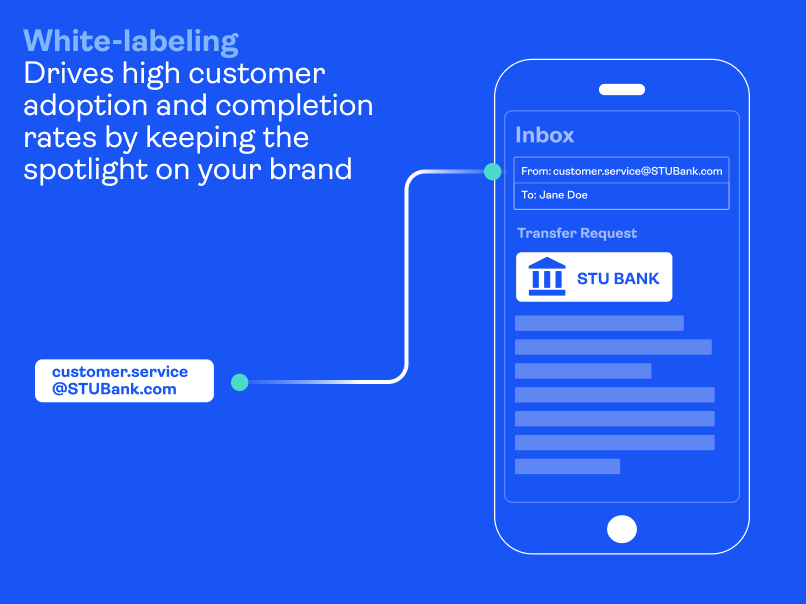
White labeling for eSignature security
White labeling is more than just custom branding. It removes all traces of the eSignature vendor’s brand and holds significant importance for two reasons:
- It creates a seamless experience for the signer. From the first invite email through the signing process, the signer engages only with your brand – not the eSignature vendor’s brand. This builds trust with your customers and leads to higher completion rates.
- It helps prevent phishing attacks. Emails generated by well-known eSignature providers have become a target for phishers and scammers to imitate. While organizations continue to add more enterprise security, email phishing scams remain a successful tactic for stealing credentials.
Amidst the urgency of the COVID pandemic, organizations hastily adopted eSignature solutions to meet the demand for remote transactions. However, numerous entities now find themselves with eSignature solutions that have increased the organization’s vulnerability to security threats.
Security researchers at Armorblox identified a phishing scheme that spoofed a common workflow email from a leading eSignature provider. The malicious email bypassed cloud and in-house email security solutions and targeted thousands of users across multiple organizations.
With a white-labeled electronic signature solution, your business can put its own brand front and center, limiting the appeal for would-be fraudsters. By customizing the content, colors, logo, and other elements of your emails, you can create a unique style that would require too much individual effort to make it worth the effort for phishers.
What to look for:
An eSignature solution that encourages you to:
- Integrate with your own email servers so the eSign emails can be sent from your domain (e.g., @yourcompany.com)
- Customize the content and appearance of email notifications
- Customize the colors, logo, headers, navigation bars, footers
- Customize dialog boxes and error messages
Cloud and data security
In addition to the criteria listed above, look at the protocols an esignature vendor has in place to identify and prevent data breaches. It’s important to understand the vendor’s security practices, certifications, track record, and the frequency of their security audits.
Performing due diligence around a vendor’s security practices and infrastructure could expose past privacy breaches, incidents of data loss/leakage, or other risks related to data security.
What to look for:
A solution that captures information about the signature process, including:
- Verify the eSignature platform uses strong data encryption in transit and at rest. It should store data in an encrypted database using strong cryptography to ensure a secure channel for all communications.
- A vendor that partners with cloud infrastructure service providers such as Amazon Web Services, IBM Cloud, or Microsoft Azure. These providers are designed and managed according to security best practices. They comply with a variety of regulatory, industry, and IT standards for security and data protection. That includes ISO 27001, SOC 2, HIPAA, FIPS 140-2, and more.
- Look for a vendor that meets additional security control and compliance requirements at the application level, in addition to the data center level. This also protects and secures customer data.
- Global data centers to satisfy in-country data residency requirements.
OneSpan solutions: eSignature security for trusted digital agreements
Seamlessly embedding security in digital workflows delivers the best customer experience and the highest completion rates.
We have 30 years of cybersecurity experience delivering eSignature and authentication solutions to financial institutions. OneSpan products ensure the security and integrity of digital documents, protecting against internal and external threats such as unauthorized manipulation and falsification. Our key product, OneSpan Sign, comes with advanced eSignature security features.
We can guide you in securing your digital agreements. Contact us to learn how to provide a trusted customer experience for any use case, channel, or geography.