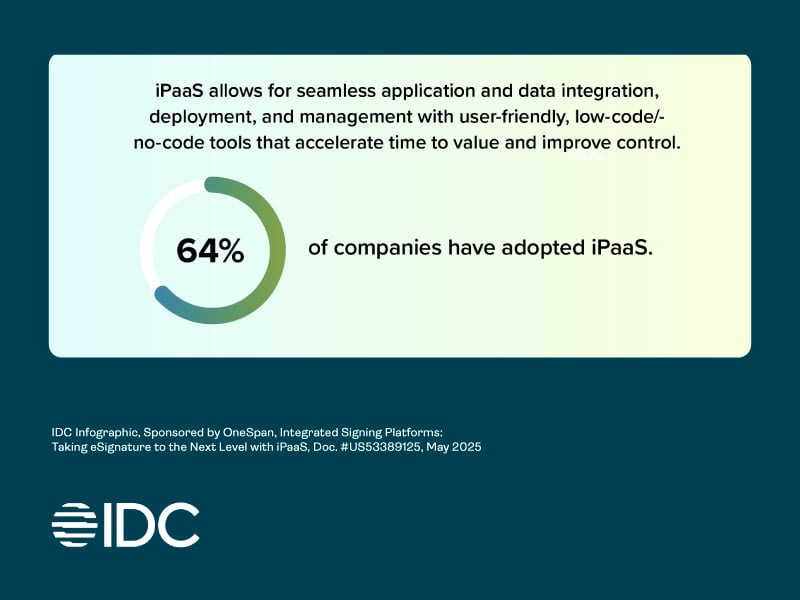
Taking electronic signature to the next level with iPaaS: Webinar recap
OneSpan and Nok Nok are reimagining authentication together

Back to identity: FIDO Alliance and the future of phishing-resistant authentication
What's ahead for passwordless authentication: Takeaways from the FIDO Alliance plenary

Improving the claims experience through modernized insurance processes

Four key takeaways from RSAC 2025

How OneSpan Sign’s Workday integration outperforms the rest