Delivering Trust Through Mobile App Shielding and Hardening

We regularly host webcasts on topics such as mobile app shielding, fraud, authentication, RASP and risk analysis to provide guidance on how to protect your customers and data. If you missed our latest webcast, Delivering Trust Through Mobile App Shielding and Hardening, here is the 5-minute summary.
As mobile devices and apps proliferate, organizations are increasingly concerned about the threats that moving to a mobile platform represents. According to a Verizon survey of 600 mobility professionals, more than 70% of respondents said risks associated with mobile devices increased over the past 12 months, and they will continue to do so in 2018.
Mobility professionals aren’t the only ones taking notice. According to Juniper Research, “over 2 billion users will access retail banking services via smartphones, tablets, PCs and smartwatches in 2018, up 10% y-o-y.” Despite this increase in mobile banking adoption, “a significant proportion of consumers are still reluctant to trust mobile services, including banking and payments.”
The reality is that banks need to embrace digital channels for growth, and customers’ trust in the mobile channel is at the heart of this digital transformation. Earning trust requires that banks secure the:
- Identity of their online and mobile users
- Integrity of the devices their customers use
- Reliability of customers’ banking transactions
Attackers typically look at opportunities for attack on two sides: the client side and the back-end. Banks have a lot more control over the back-end and can more effectively ensure that their infrastructure meets security standards, making successful attacks more difficult. Mobile banking apps, however, reside on customers’ devices, which is an environment largely outside of the bank’s control. And despite efforts to secure the platform, users become the weak link. After all, some users will engage in risky activities including:
- Jailbreaking or rooting their devices in order to download free apps
- Connecting to free networks regardless of their trustworthiness
- Postponing critical security updates to their operating system
This creates a big challenge in preventing mobile banking fraud. Mobile transactions are still in the Wild West, and the above factors play a significant role in whether banks can trust the devices on which their mobile banking apps are installed.
At the end of the day, banks and financial services providers are under tremendous pressure to meet customer expectations for secure, convenient, and easy mobile experiences. But, the mobile channel has become the target of choice for cybercriminals and attacks on banking apps are at an all-time high. So, how do banks reconcile these competing forces and build trust in the mobile experience?
Let’s look at mobile app shielding and hardening as one way to do that.
Mobile App Security Threats
Last year was a wake-up call for mobile developers concerned with the security of their apps. We saw numerous indicators pointing to a massive spike in the growth of mobile security threats, including:
- A 72% increase in unique mobile malware samples collected by McAfee Labs
- A 70% increase in the number of apps that Google pulled off its app store
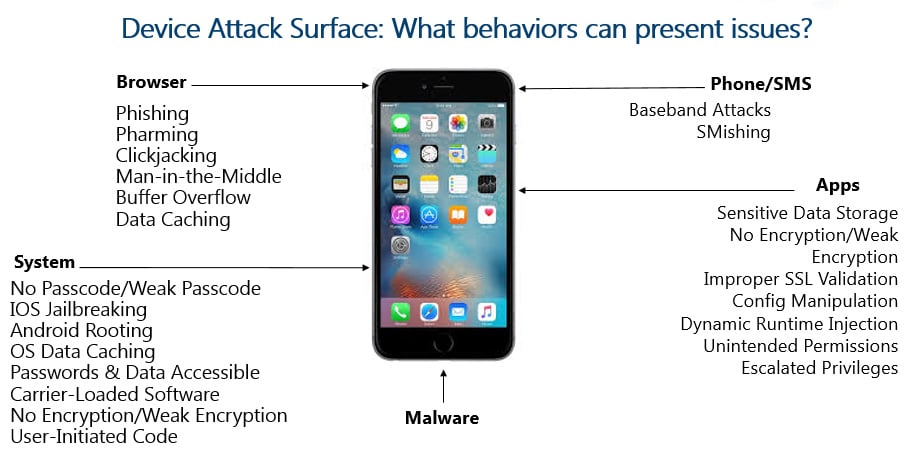
In addition, mobile malware is becoming more complex and sophisticated. Today mobile malware is more than just creating fake mobile apps. It can leverage the actual program code that every app uses. This means that apps themselves — even those that have been carefully crafted — can be a threat.
Examples of advanced threats to the mobile environment include:
- Corruption of the execution environment: When the application sandboxing is broken on a rooted device, the data stored on the device can be read or updated by any other application running on the same device. (For example, with root access, malware can access the user’s banking credentials)
- Reverse engineering of the application: Through instrumentation and debugging, malicious actors can modify the core functionality of an app, or they can create an exact duplicate of the app. Either way, the malicious actor will then publish the app to an app store for victims to download and install. During installation, the modified app will typically silently install malicious apps that steal data from the user and the user’s environment.
- Modification of the application: Modified and repackaged applications are published on an alternative store for download by victims of phishing attacks. Crypto-mining malware is being packaged with many redistributed applications.
Creating a Trusted Mobile Environment
Many applications are developed without a strong focus on security, so adding security to daily development life is the first step to creating a trusted mobile experience. Developers are often given specs for the functionality of the application, but specifications for secure code are not always a part of the product definition. Plus, secure coding standards can vary depending on the specific coding language and the libraries being used for the application development.
It can be tempting for developers to seek out third-party libraries to leverage workflow and code to solve specific problems. It may make life easier, but developers can get into trouble if they assume that code has been reviewed for security holes. When considering this option, developers face four choices on what to do next:
- Ignore security completely (not a good idea)
- Use open source modules (which are rarely reviewed from a security/risk perspective)
- Do it yourself (and hope the mobile app is secure)
- Use commercially available API libraries that are purpose-built to protect mobile applications
As a best practice, we recommend using API libraries that are purpose-built to protect mobile apps. Using a vendor’s APIs frees developers’ time to work on the features and functions that are important to customers, while the vendor’s technology safeguards the app. This one change in development habits can go a long way towards creating a trusted mobile environment.
What is App Shielding?
Mobile malware comes in the form of malicious programs and key loggers, but it can also be found hidden within the code of libraries and embedded in applications. To solve some of the issues with insecure apps, we must therefore consider the security of the mobile app source code itself. This calls for a new kind of app protection, something that works from inside the app. This technology is called app shielding.
App shielding and hardening is a set of technologies used to add security functionality directly to mobile applications for the detection and prevention of application-level intrusions. To accomplish this goal, app shielding does four things:
- Proactively shields applications from malware
- Controls execution and prevents real-time attacks
- Protects mobile apps to ensure data and transactions are not compromised
- Maintains a mobile application's runtime integrity, even if a user inadvertently downloads malware onto their device
App shielding is part of the OneSpan Mobile Security Suite solution, which contains a number of libraries that can be used to quickly enhance the features of a mobile app. Our mobile app security APIs also provide an automated implementation process. This allows banks to quickly release secured apps without affecting the development timeline.









