
PSD3: Habemus Pactum

Securing identity in the age of agentic commerce
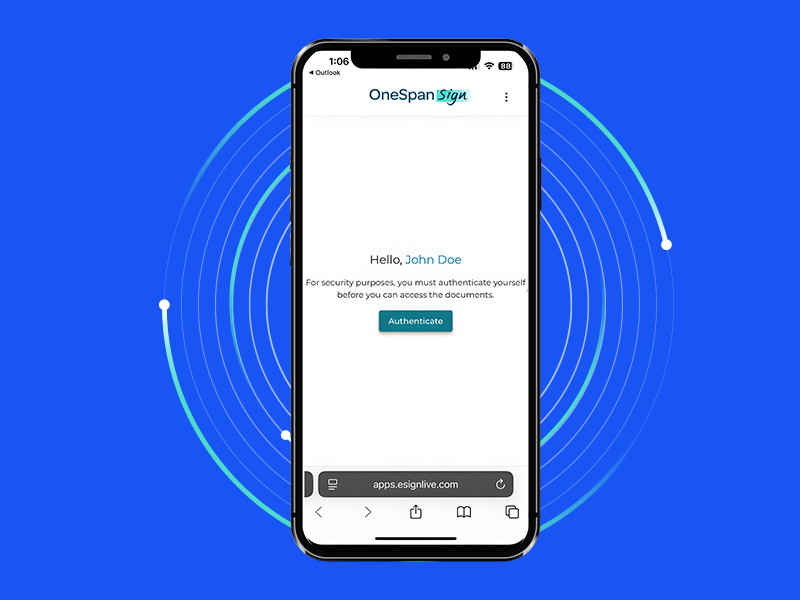
eSignature security tip: How to protect your signing URLs against cyberattacks
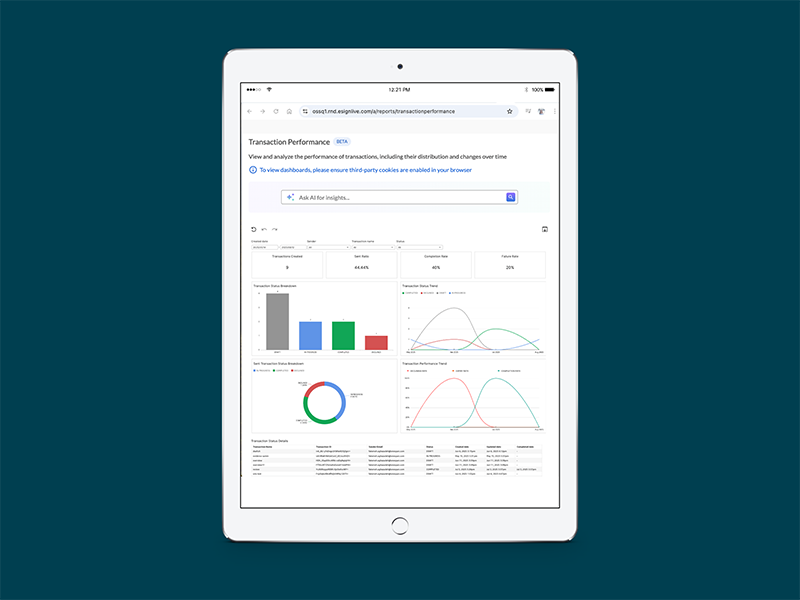
AI Answers and Dashboards for smarter digital transaction management

FIDO Authenticate 2025: What I learned about passkeys at scale

How CURE Auto Insurance digitized with OneSpan Sign for Guidewire InsuranceNow
How we automated HR processes with our own eSignature software








