What Banks Can Do to Protect Against the Krebs-reported Vishing Scam

I recently came across an interesting article by Brian Krebs that got my attention.
In this article, “When in Doubt: Hang Up, Look Up, & Call Back”, Krebs tells the story of one of his readers, aliased "Mitch", who was defrauded for $9,800. It caught my attention, because Mitch is a seasoned cybersecurity and tech-savvy reader. You would not expect him to fall for such scams.
The article provides guidance on what people can do to protect themselves from vishing scams, but it doesn’t explore how the bank could have detected or prevented the attack. In this post, we’ll do just that. I recommend you read Krebs’ full article linked above, but I do provide a summary of the scam below. If you've read the article already, skip the next section and dive into my analysis of the attack.
Summary of Brian Krebs’ Article: “When in Doubt: Hang Up, Look Up, & Call Back”
Mitch received a call from what seemed to be his financial institution, warning him about fraud detected on his account. Mitch’s first instinct was a good one. He verified that the number used by the caller matched what was printed on the back of his debit card. Being security-savvy, Mitch knew that scammers could easily spoof this phone number. At the same time, he checked his online banking while on the phone. Mitch saw some fraudulent charges and ATM withdrawals. Because the caller didn't ask for any personal information during that call – and instead reassured him the bank would reverse the charges – Mitch took it as a genuine call from his bank.
The next day, he received another call about fraud on his account. Because something seemed off about the call, he decided to call his bank's customer service department while keeping the first call on hold. Somehow the representative was able to check and confirm that there was another call active with Mitch. This convinced him that he was indeed speaking to his bank.
The caller then told Mitch they would send him a one-time password (OTP) via SMS text messages to verify his identity. This was something the bank had done in the past, so Mitch agreed. He received the OTP and read it back to the caller. The following Monday when Mitch checked his online banking, he saw a $9,800 outgoing wire transfer posted on his account. He later found out the wire transfer went to an online bank account created in his name by the cybercriminals.
My Analysis of the Vishing Attack
The scammers used a skimmed card to initiate an elaborate social engineering scam in order to steal sensitive information, account numbers, and money from Mitch. They had also managed to commit identity theft and open a new bank account in Mitch's name, which we'll see later allowed them to bypass the transaction from being flagged by the bank.
Can we blame Mitch for falling for the vishing calls? I don't think we should. While Mitch made some small mistakes, he displayed good reflexes. Mitch called his bank right at the outset, knowing cybercriminals could spoof the caller ID.
It's important to realize that Mitch has more industry knowledge about scams and social engineering than most people, and yet he still fell for it. Knowledge and awareness were not enough in this case. To prevent these scams from impacting other customers in the future, the bank can leverage sophisticated detection and prevention tools.
Here are four areas of opportunity where the bank could improve their fraud prevention strategy and stop future vishing and fraud attempts:
- The bank relied on a one-time password sent over SMS to validate a payment submitted by phone banking.
- The bank’s fraud detection system did not consider the customer's usual behavior and channel usage.
- The fraudulent payment was not flagged, because the beneficiary account was in the same name as the payer’s account. Their fraud detection system did not consider whether the customer had previously used this beneficiary account or not.
- The bank had inadequate monitoring and verification controls in place to identify and validate a suspicious payment or action on the account.
How Could the Bank Have Protected Mitch Better?
One-Time Passwords Sent Over SMS vs. Dynamic Linking
Using SMS one-time passwords to secure an online bank account is not a good practice. On top of that, using SMS OTP to validate payments is worse. SMS one-time passwords are prone to phishing, vishing, social engineering, mobile malware, and other attacks. Plus, they provide no context for the transaction. Context is important, as this case demonstrated, because it provides the customer with knowledge of what the one-time password is being used for.
In Mitch’s example, the OTP was being used to authenticate the wire transfer of $9,800 initiated through phone banking. However, when he received the one-time password, he was told it was to verify his identity. Mitch had no way of knowing that this same code could be used by an attacker to post a payment on his behalf. Two key changes could have probably prevented this attack and many similar vishing and phishing attempts:
- Dynamic linking: Dynamically linking a one-time password to a payment or action makes this OTP only usable for that specific payment or action. Additionally, when applying dynamic linking there should be context provided to the user about what this OTP is being used for. In our example, that means the one-time password should have been linked to the payment and the payment details should have been visible to and reviewed by Mitch before inputting the OTP anywhere.
- Using a secure channel of communication: This ties in perfectly with the previous point. Instead of relying on a vulnerable channel such as SMS, the bank could have leveraged technology to provide a software-based authenticator to their customers. The authenticator can be a standalone application or even integrated with the mobile banking application. Instead of sending the customer an SMS to a mobile number that could have been taken over (using SIM swap attacks) or stolen by mobile malware, the bank can establish a direct channel of communication with the user via their own mobile app. This allows the bank to implement additional protection on the communication, by leveraging end-to-end encryption as well as device analytics.
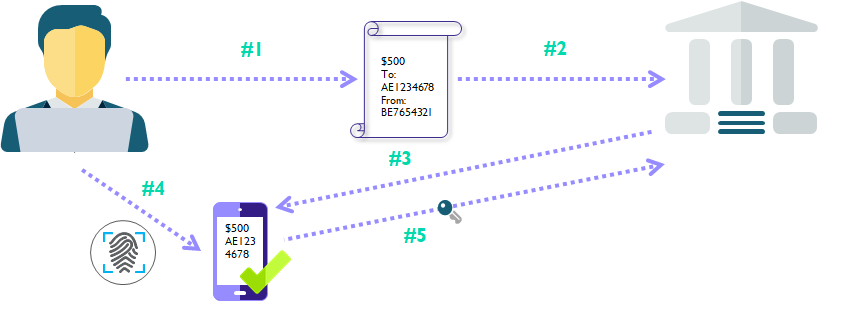
With dynamic linking, the transaction or operation details are part of the one-time password generation and validation process. The user is presented with the details when generating the OTP and the OTP can only be used to validate this specific operation. Dynamic linking is a key tool to fight phishing and social engineering as it provides context to the user when they are authorizing an operation or transaction.
If the bank would have implemented the changes mentioned above, instead of receiving a one-time password via SMS, Mitch would have received a push notification on his phone.
- Upon opening the notification, the app would have asked Mitch if he would like to authorize the following payment (and would have displayed the payment details).
- Mitch would then be required to verify and confirm the authorization with a PIN or biometric.
- The app would have generated a one-time password automatically and sent it back to the bank.
- Even if the password was intercepted, due to dynamic linking it can only be used to verify the payment that Mitch just reviewed – nothing else. Therefore, an attacker wouldn't be able to use it.
Usual Customer Behavior and Channel Usage
While dynamic linking and secure channels would help to stop a lot of common attacks, there's more that can be done to protect the bank’s customers. In our example, it doesn't seem like Mitch is a common user of phone banking. He tends to favor the online banking channel. The bank could have used this change in Mitch's usual behavior from online banking to phone banking, combined with a significant transfer to an account Mitch has never transferred to, as an indicator of fraud. The bank could then have carried out additional verification before processing the payment.
Payer Account and Beneficiary Account under the Same Name
Our third point is an interesting one, because it demonstrates the attackers may have had insight into the bank's processes. It turns out they transferred the funds to an account opened in Mitch's name at an online bank. The bank then used this account information to automatically greenlight the payment. This means his bank calibrated their fraud detection solution to place a level of trust on the onboarding process of another financial institution— a process over which they have no control. Identity theft is a common occurrence, and financial institutions cannot rely on each other to exempt a payment from further controls.
Inadequate Monitoring and Verification Controls
The last point is speculation, but there are signs the bank’s fraud monitoring process is not mature. It could even be that they have the right tools, but they don't know how to use them correctly. One indicator for me is the fact they automatically allowed that payment, because it went to an account in the same name.
Another concern is that the fraud monitoring system did not take action on the fraudulent credit card charges, because the attackers managed to place a travel notice on the account. This travel notice informed the system to disregard all geographical alerts associated with his credit card number for that time.
However, note that Mitch accessed his online banking account when the fraudsters called him. This means the bank could have noticed Mitch is logging in to his online banking from California while using his card in Florida. This type of cross-channel information is often not correctly utilized by banks but can be extremely valuable in identifying fraud. If anything, this could have triggered a deeper investigation by the fraud department which could potentially have identified the ongoing scheme.
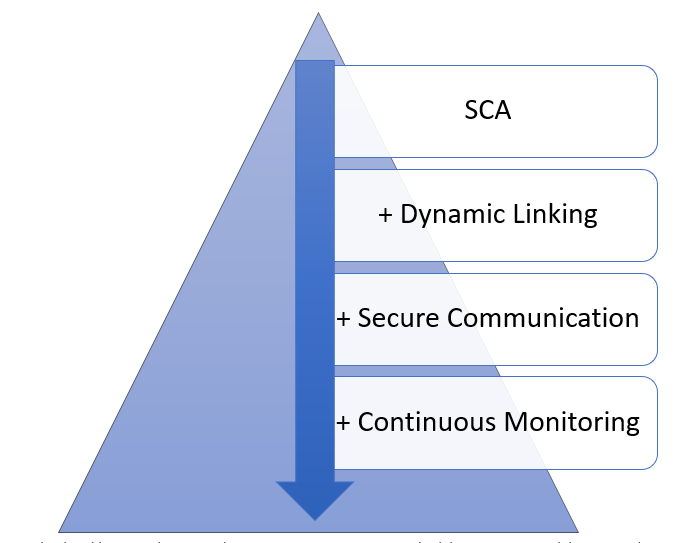
Defense in depth: adding complementary layers increases an organization’s ability to prevent and detect attacks.
Explore a Multi-layered Approach to Security
Fraudsters are always working to devise new strategies to circumvent fraud teams, and this example in the Krebs article testifies to it. For that reason, it is essential that financial institutions leverage more sophisticated fraud detection and prevention systems. With the right system and security tools like dynamic linking coupled with a secure communication channel and continuous fraud and behavioral monitoring, banks can protect customers from sophisticated social engineering schemes as well as other types of fraud attacks, including phishing, malware, and more.









