More Trust, Less Mobile Fraud: How to Offer a Safer Mobile Banking Experience

Trust is an essential component of the mobile banking channel. It seems simple: a bank needs to trust that the person sending a transaction request is a legitimate customer. And vice versa, a customer needs to be sure that the communication they receive on their Android or iOS mobile devices in regard to that transaction, really comes from their bank. But is building trust in the mobile channel really that simple? And what can financial institutions (FIs) do to prevent fraudsters from abusing this trust with malware, account takeovers, identity theft, and other types of fraud?
More Users, More Mobile Fraud
It is obvious that COVID-19 has changed the way we interact with banks. Mobile banking is on the rise. A recent Aite Group survey found that 86% of senior millennials, 83% of young millennials, 72% of Gen Xers, 38% of baby boomers, and 17% of seniors gain access to their banking accounts using their mobile phone at least once a week. Even mobile corporate banking transactions are increasing in volume. Citi reported a tenfold increase in users of its corporate mobile banking app, CitiDirect BE, in March 2020 when compared to the same month a year earlier. While the recent surge in mobile banking has been largely attributed to COVID-19, this growth in mobile banking use will continue beyond 2020.
Fraudsters follow opportunity and the path of least resistance. That opportunity is currently in mobile and, not surprisingly, we have seen a sharp increase in fraud attacks. Industry experts report a 37% increase in mobile phishing attacks globally in Q1 2020 compared to the previous quarter and a 173% increase in mobile banking Trojans for the same period.
These fraud attacks are also becoming more complex, including multichannel attacks that combine different techniques, where compromised mobile devices play a big role. In the case of these attacks, FIs will notice that anti-fraud strategies that worked in the web channel, won’t be equally effective in mobile banking.
More Services, More Data
In the last couple of years, we have seen a tremendous evolution in the mobile banking channel towards offering more services, including higher-risk transactions. The industry has now seen the emergence of mobile-first digital banks and mobile-only eMoney institutions. Mobile devices are no longer used only to check the bank account balance or transfer small sums. They are becoming our digital identities, used as multi-factor authentication tokens across multiple banking channels. They offer convenience and opportunity for anytime, anywhere interaction with bank accounts and FIs.
FIs, however, cannot manage all the components of this interaction. The mobile device used by the customer serves other purposes, including entertainment, social media, phone number, SMS text messages, household management, and shopping. The banking app is often installed on a device with tens of other apps coming from various sources and developers on and off the official app stores. Depending on the customer’s security awareness and personal actions, this device can potentially be jailbroken/rooted, it can contain malicious apps or can be shared between more users. The device owner could mistakenly install a fake banking app from the app stores, too. In other words, the actual security status of each customer’s mobile device will differ; it fluctuates and can change at any time. This is a challenge for FIs: How to ensure that their mobile apps can operate securely in these risky conditions?
In regard to the security of the mobile banking app, mobile application shielding empowers it to operate safely in untrusted environments without interrupting the user experience. It strengthens the app and allows it to run securely even on rooted/jailbroken devices. Data analysis is another important aspect. A remote banking channel, such as mobile banking, offers a significant amount of user-, device-, and transaction-related data. This covers both the data exchanged between the device and the bank’s server during each transaction, as well as a wide array of data collected from the mobile device in a more general context. FIs need to find ways to leverage this wide range of data to continuously assess the level of trust and transaction risk.
Establishing Mobile Trust
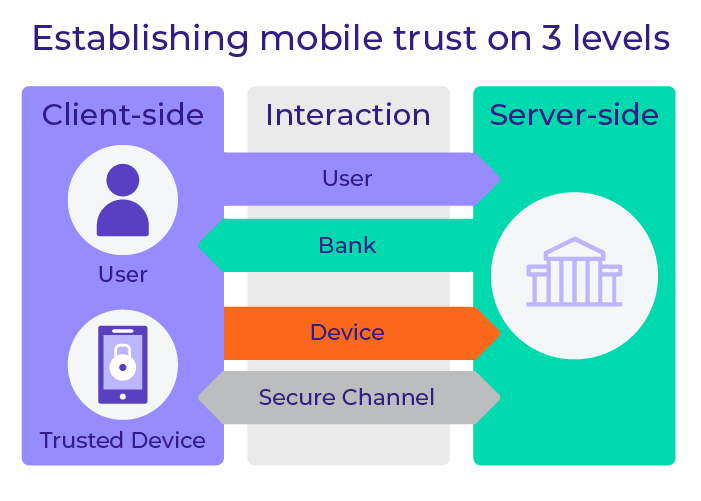
Trust is at the core of an FI’s digital growth strategy. An FI needs to trust that it knows the user and that it can securely provision that known user with a strong credential that is easy to use as part of a two-factor or multi-factor authentication (MFA) strategy. It also needs to trust the intent of the user, whether for a financial transaction or process assurance as information is exchanged. Trust needs to exist also in regard to the user's device and the application they use. It’s also important to trust the communication channel to/from the trusted identities, devices, and applications. Last but not least, FIs also need to have insight into and establish trust regarding the user’s behavior on all their devices across all the banking channels.
Creating and maintaining this trust involves actions at the following levels:
- Client-side: improving the security of the customer’s mobile device
- Server-side: analyzing the data in the background
- Communication channel: establishing trust between the mobile device and the bank to enable secure interaction in both directions
A trusted environment on the client side can be achieved by:
- Creating a secure link between user and device with a set of provisioning tools
- Securing the integrity of the app – for example providing developers with the tools to securely store data inside the app
- Shielding the app to protect it against runtime attacks
- Evaluating the risk and context of the device (e.g. jailbreak, geolocation), since the mobile banking app is installed on a shared device
A trusted interaction is established by:
- Authenticating the device
- Authenticating the user
- Authenticating the bank
- Providing a secure channel for the interaction
A profile on the server side is established by:
Looking at each interaction independently and analyzing all the available data provides the ability to create a user profile and a device profile on the server side and to build a timeline to identify abnormal activities.
When trust exists at these three levels, through a 360-degree approach to mobile security and fraud analysis, FIs can offer a rich mobile banking experience. For example, users can access more features within mobile apps that would not be available otherwise for security reasons (e.g. applying for additional bank accounts or sending larger money transfers).
Establishing and managing this trust requires a lot of data analysis. This is where a fraud prevention system based on risk analytics and machine learning plays a vital role. It works by gathering, in a transparent and continuous manner, a broad range of mobile-specific data. It is important to collect and analyze data that includes elements characteristic of the mobile channel. Because mobile phones in general provide much richer context and enable more advanced analysis, leveraging the broader context of the mobile channel is essential for fighting mobile fraud.
For example, this data can include:
- Device health – detecting, among others, if the device has been jailbroken or if there has been any suspicious activity. This helps evaluate the risk related to user actions originating from this device and adjust the necessary security measures.
- Insight into authentication and biometrics, such as face recognition score or PIN strength. This helps the risk engine decide whether the authentication measures that have already been applied are sufficient to trust the user identity.
- General device information, such as the version of the operating system, device model, etc. This helps detect sudden device changes, which can be an indicator of an ongoing fraud attack.
A Trusted Mobile Device
A trusted mobile device enables FIs to expand the scope of services offered via the mobile channel. Continuous evaluation of risk gives more confidence to FIs concerned about sophisticated mobile fraud attacks. With a risk analytics engine, FIs can confidently enable any use case, from increasing the transaction limit to allowing existing customers to open a new deposit account.
A trusted mobile device also supports use cases beyond accessing mobile banking. When the FI applies security measures that allow for the right amount of trust, the device can double as a multi-channel authentication token. It can be used to securely sign transactions for online banking or to approve funds withdrawals from ATMs. With the continuous analysis of hundreds of data elements in real time using machine learning, FIs can offer that level of trust.
To enable the notion of a trusted device, an anti-fraud solution needs to operate with a broader, holistic approach that combines different elements:
- Secure data collection and storage
- Secure channel for data transfer from the mobile device to the bank’s server
- Secure application and server-side analytics
These elements create a full and reliable picture of the customer’s device by determining a risk score. The score has to be continuously assessed, and controls have to be in place to react in case the risk level increases.
Continuous Trust Management
As mentioned before, the level of trust of a mobile device can change at any moment. This is why it is so important to:
- Dynamically evaluate trust associated with the device.
It is not enough to establish the level of trust when a user begins their banking session. On a BYOB device, the state and condition of the device can change any minute (e.g., if a user installs a suspicious app). This can create risky circumstances in which neither the FI nor the user is controlling the banking transaction any longer. - Instantly react to any changes to the environment in which the banking app is operating.
The FI’s role is to maintain a live assessment of the situation and to step in immediately when there is a justified suspicion that the device (and therefore the banking session) has been compromised, for example by malware. - Verify the user’s digital identity in a transparent and continuous manner.
In addition to monitoring the environment the banking app is operating in, FIs also need to confirm that they are dealing with the legitimate user throughout the whole session, to prevent a situation in which a fraudster takes over after the user has successfully logged in. The FI needs to look for any clues that the transaction request is not coming from the right person; they can do that by assessing the behavioral context.
Does this mean FIs can simply deny access to the services when the trust level decreases? In our opinion, a rigid approach to device trust would drive away a large segment of mobile banking users. These days, many mobile devices are jailbroken or rooted. The fact of such a device being used in the mobile banking channel will raise a flag in the fraud risk analysis and FIs may be tempted to shut the application down. But this would frustrate mobile customers, likely prompting them to switch banks. Instead, pairing risk analytics technology with application shielding and other mobile security technologies can help prevent fraud while increasing customer satisfaction and trust. These technologies will identify the risk factors but still allow the mobile banking app to function securely in an otherwise risky environment.








